by Daniel Brodie, CTOand co-founder of Cynerio
For many in the cybersecurity community, “the perimeter is dead” has evolved from a peripheral warning to a statement of fact. In today’s decentralized threat landscape, perimeters are at best amorphous and more commonly irrelevant. This is particularly true in healthcare facilities.
With an unquantifiable amount of interconnectivity across healthcare ecosystems, maintaining security or even minimal levels of cyber hygiene has become increasingly complex. Firewalls and VPNs just don’t cut it anymore, and as the perimeter grows more trivial, Zero Trust has emerged as the rising star of security frameworks.
What is Zero Trust?
A NIST report released in August 2020 defines Zero Trust as an “evolving set of cybersecurity paradigms” that shifts the focus from static, network-based perimeter defense to dynamic defense that views every entity as a potential threat:
- Users—people; employees, guests, or threat actors
- Assets—devices and systems
- Resources—sensitive data; e.g. ePHI/PII, social security numbers, etc.

Traditional security frameworks set policies to block access to networks and entities. Zero Trust operates on the adage of “never trust, always verify,” and blocks access to all entities from the start. It assumes breaches are always in progress and grants access on an individual basis for specific communications at specific times only after each entity has been verified and authorized.
This approach limits lateral movement and removes the conventional reliance on firewalls and VPNs as primary security solutions. But blocking all communications until they can be authenticated, as directed by Zero Trust, will disrupt critical medical workflows and could affect device functionality, neither of which can be tolerated in healthcare settings.
Healthcare IoT cybersecurity challenges
Healthcare IoT devices are uniquely difficult to secure for many reasons, and these challenges must be addressed when configuring a healthcare-safe Zero Trust policy:
1. Unmanaged devices
Healthcare facilities have thousands or even tens of thousands of unmanaged medical and IoT devices that are invisible to the network. Many were never developed for connectivity and have zero built-in security features.
2. Clinical impact
Healthcare IoT devices with the highest clinical impact are used in medical treatment, while other factors that affect impact scores include vulnerabilities like open ports, weak or default passwords, outdated firmware or legacy operating systems, and required communications with external endpoints.
When it comes to implementing Zero Trust policies, rating devices’ clinical impact is crucial to identifying the most vulnerable assets on the network. It also helps prioritize which devices Zero Trust policies should be enforced on first, in order to minimize the effect on operations.
1. Unrecognized healthcare protocols
Healthcare IoT devices often run obsolete, unauthenticated, and/or unencrypted protocols and lack access controls. This poses a number of challenges:
- Standard IT security tools don’t recognize IoT-, medical-, or vendor-proprietary healthcare protocols (e.g. HL7, DICOM, POCT1-A, ASTM, VOXP, BACnet, Modbus, LonWorks, MQTT, PJL, MNET, etc.), and they don’t understand how medical and IoT devices communicate.
- Standard tools can flag necessary connections between Healthcare IoT devices as anomalous and set policies to block them, which can disrupt clinical workflow and jeopardize patient safety if the devices are used in care delivery.
- In cases where devices do have authentication protocols in place, they’re often outdated, stand-alone, and not integrated with the hospital’s Identification Management infrastructure, making it impossible to authorize and authenticate communications. To further complicate matters, these credentials are hardcoded and difficult to update (i.e. warranties may be invalidated if hospitals update without coordinating with vendors).
2. Devices are insecure by default
Many medical and Healthcare IoT devices come out of the box with inherent vulnerabilities. These devices have insecure open services used for remote support, management, and monitoring. These services are configured by default to allow connectivity with minimal authentication, if any (e.g. Radiology devices arrive with open Telnet or RDP services).
3. Required vendor and cloud connections
Many devices must connect to cloud services and third-party vendors to function properly. This makes blocking devices from all internet access impossible without risking patient safety or disrupting clinical workflow. To add fuel to the flame, any connection with third parties risks exposing ePHI and vulnerable devices to threat actors, and VPN connections are no longer a failsafe security option, because healthcare facilities have no control over the security of third parties.
4. Long set-up times
Time itself is a vulnerability due to rapidly changing network topologies and the risk of disrupting device functionality and medical services if communications are blocked, but Mapping and profiling Healthcare IoT assets just in preparation for setting up sound security infrastructures can take months or even years without the aid of an automated solution due to:
- Devices’ unique communications patterns: some communications are sporadic (e.g. vendor connections), and many are unmanaged and/or invisible to the network, as discussed above
- Lack of documentation on which communications should be authorized or not
- Fear of disrupting medical services–setting up sound security infrastructures must be done meticulously to ensure operational continuity
4. Steps to achieving healthcare-safe Zero Trust cybersecurity
Step 1: Identify what needs to be secured
- Take inventory. Ensure all assets are accounted for at all times.
- Understand what you need to protect: (1) patient confidentiality, devices that contain ePHI and other critical patient information; (2) patient safety, i.e. medication dosages, glucose readings; (2) medical services and clinical workflows, device functionality and network topology.
- How valuable is the information stored on devices and how vulnerable are the devices that store, receive, and send it? How often are the devices used and are they mission-critical? What is the device’s organizational impact on the healthcare facility?
Step 2: Map data flow across the network
- Analyze network and asset behavior, consider healthcare-specific protocols to identify risks and vulnerabilities.
- Conduct an in-depth inspection of clinical workflows to understand what communications are essential to operational continuity.
Step 3: Define and enforce policies
- Determine who needs access, when they need access, and why. What server does the device communicate with? Which vendors does the device need to communicate with for maintenance services?
- Determine entities’ identities: What is the asset? What is it used for? What resources does it contain, send, or receive? Who’s using it?
- Configure healthcare-safe Zero Trust policies that support operational continuity by ensuring access to critical medical devices and authorized, verified, and authenticated vendors:
- Configure and enforce North-South segmentation policies to block all unnecessary external communications, including unauthorized vendor and cloud connections. This will help prevent ePHI exfiltration and hinder malware’s ability to penetrate the network.
- The most vulnerable network is a flat network. Configure and enforce East-West and microsegmentation policies to limit lateral movement.
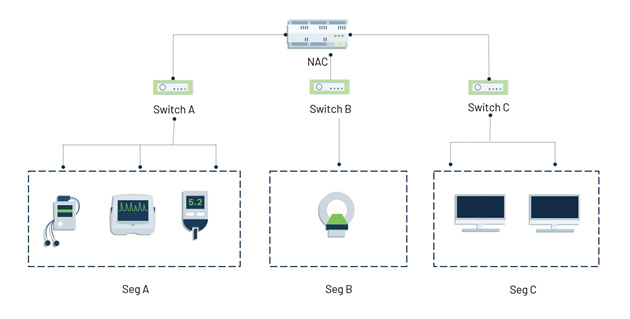
Step 4: Monitor network traffic
- Networks are dynamic and therefore require ongoing maintenance. Traffic must be monitored continuously to immediately identify anomalous traffic, update policy, and block malicious communications.
Despite the many obstacles faced by Healthcare IoT networks and devices, a judiciously designed Zero Trust policy infused with clinical context can protect healthcare environments from threat actors and ubiquitous vulnerabilities while guaranteeing operational continuity and patient safety.
About the Author
Daniel Brodie is the co-founder and CTO of Cynerio, Inc., an AI-powered platform that enables healthcare providers to secure patient data and connected medical and IoT devices against cyber threats. Daniel is a world-renowned cybersecurity expert and technologist known for his expertise in application and operating system security and vulnerability discovery. He has led multiple Black Hat talks on threat intelligence, malware detection, and encryption.


