NeuShield Data Sentinel Review
Visit Website| Ease of Use: 9.9 out of 10 |
Overall Review Score
0.00
|
| Platforms Supported: 9 out of 10 | |
| Features: 9.8 out of 10 | |
| Customer Support and Documentation: 9.4 out of 10 | |
| Pricing: Score: 9.5 out of 10 |
Ransomware has become one of the largest problems in cyber security. Ransomware is a type of malware that blocks access to your data by encrypting or hiding it. To get it back, you must pay the criminal a “ransom.” After the attack, you have to spend valuable time restoring data—if you have viable backup. If not, you have to rebuild your computer from scratch. And if you run a small business, you may face potential lawsuits from customers who have lost access to data and services.
Enter NeuShield Data Sentinel, receiving a very high score and our praise for focusing solely on this problem, in an innovative and easily deployed way. Every endpoint, from your home computers, to the Small Office Home Office (SOHO) to the Small to Medium Sized Business (SMB) cannot afford to be without this product.
NeuShield Data Sentinel is designed to allow customers to quickly recover from ransomware that most anti-virus and other endpoint security software might miss. Other security products cannot detect or block all ransomware attacks, allowing sensitive data to be encrypted. Backup products were never designed to protect from ransomware, and it can be time consuming and costly to reimage a device and restore data after a ransomware attack. NeuShield can get all the user’s data back in seconds, no matter how much was encrypted by the ransomware.
Please note: NeuShield Data Sentinel complements and runs along side your existing antivirus software to fortify your computer and protect important data. NeuShield Data Sentinel is compatible with most antivirus solutions and endpoint security platforms.
Ease of Use: Score: 9.9 out of 10
This product is extremely easy to install and use. There are not a lot of user interface elements and they are all straightforward. Professional or institutional users should not encounter any difficulties. There are just a couple of options, like adding protected folders and enabling or disabling boot protection. Also, there is a single button to reboot or restore the system. It’s worth noting that some routines are unique in the market and it may take a short time for some people to understand their concept and function.
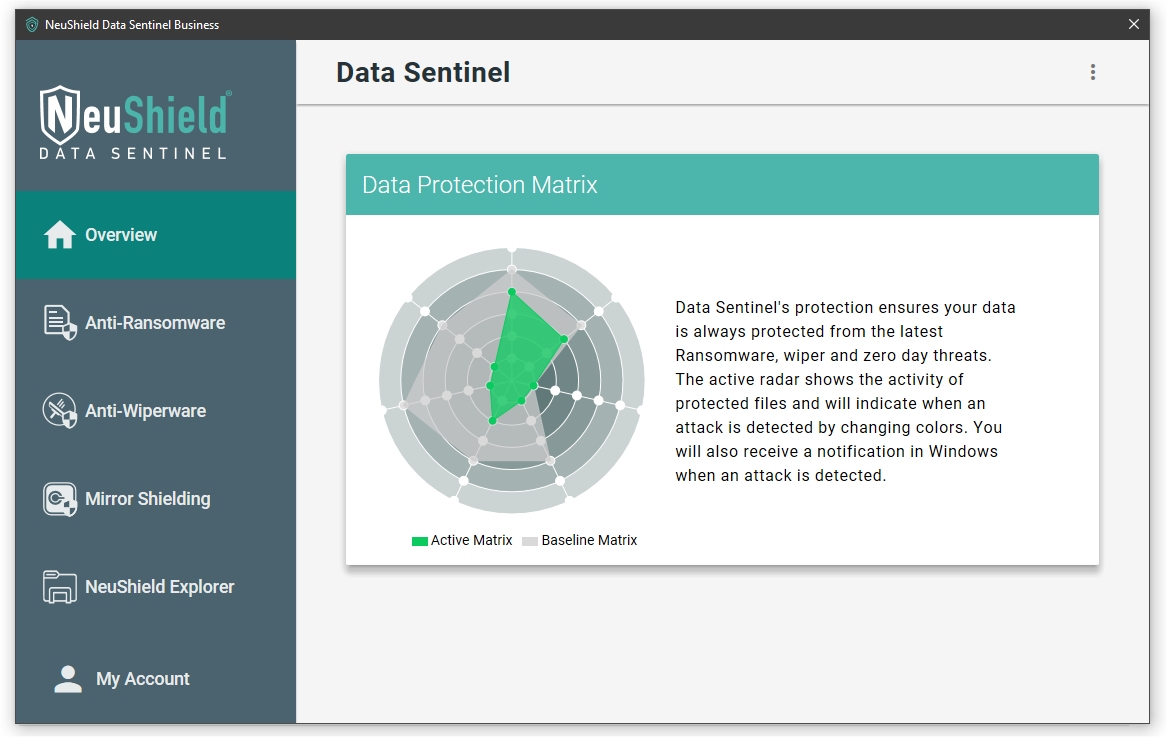
NeuShield runs transparently in the background. By default, the product protects all the common user folders, such as the Documents and Desktop folders. When you first load the graphical user interface (GUI), you see a dynamic matrix with some basic information. There are tabs on the left side of the GUI to allow the user to add protected folders, modify settings, such as the boot protection or load the NeuShield Explorer. It also has integration with Windows Explorer allowing you to right-click on protected files or folders to revert the folder or restore files back to a previous version.
There are three ways that NeuShield Data Sentinel uses disk space. The first is for basic product installation, which requires around 50 MBs of hard disk space.
The second way that NeuShield uses disk space is for protected files. The amount of space used here will vary from system to system depending on how many protected files are modified. Typically, NeuShield uses about 10% additional disk space, based on the size of the protected data. For instance, if you have 100 MBs of protected data then NeuShield will typically use around 10 MBs of additional disk space.
The third way that NeuShield uses disk space is for One-Click Restore. For this, NeuShield will use up to a maximum of 10 GBs of disk space. The amount of space actually used for One-Click Restore will vary depending on certain factors, such as available disk space. For example, once the system is running low on disk space some of One-Click Restore’s snapshots may be deleted to free up disk space.
Cloud-based Console: Score: 9.5 out of 10
The NeuShield Portal is a way to monitor and manage your NeuShield clients online. From the Portal you can view status of your clients, configure specific client settings, view license status, update license keys, download client software and activate new clients.
First you login:
 Then you manage your protected devices:
Then you manage your protected devices: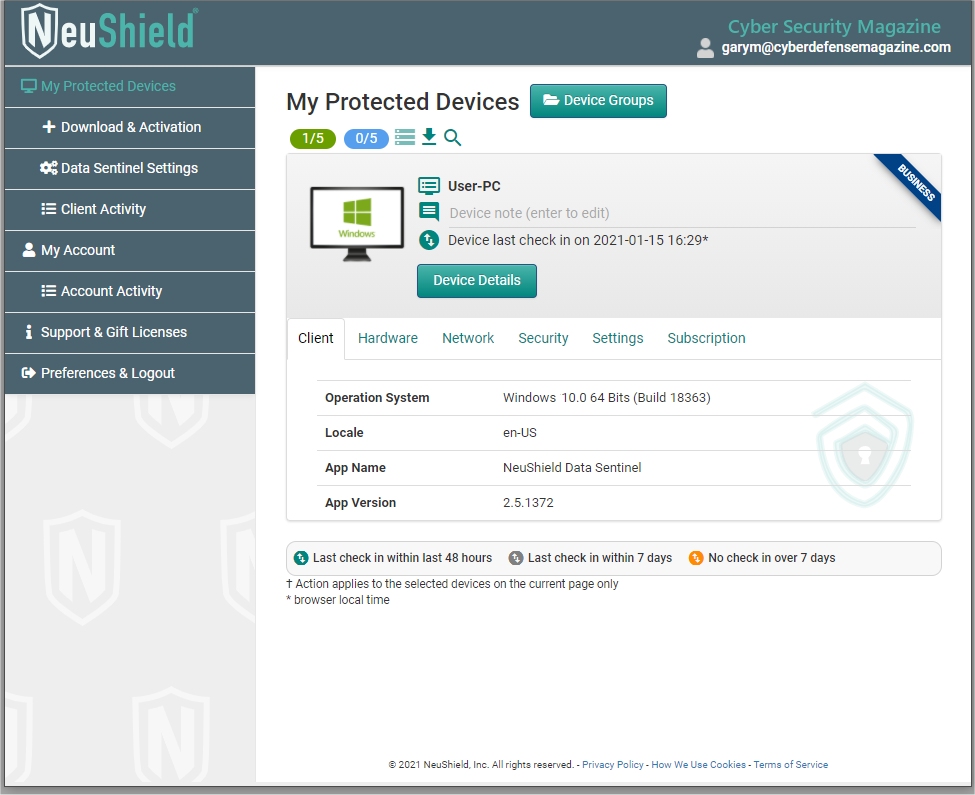
From the NeuShield Portal you can change settings for your clients. Changing these settings will affect all clients in that account.
Auto Update Settings
By default, NeuShield Data Sentinel will automatically update to the latest build. However, this can be disabled from the ‘Data Sentinel Settings’ panel on the NeuShield Portal.
Anti-Wiper & Boot Sector Protection
Anti-Wiper and Boot Sector Protection are features that can be modified by the end user, by default. However, if you want to control the options from the NeuShield portal you can set these options to ‘enabled’ or ‘disabled’ which will overwrite the user settings for these options.
Maximum Number of Data Engrams
Data Engrams are backup copies or revisions of protected files. You can configure the maximum number of Data Engrams to store. Changing this number will not remove existing Data Engrams. So, if for example a file has 10 Data Engrams then changing this number to 5 will not remove those 10 Data Engrams. However, it will prevent other files that have less than 5 Data Engrams from creating more than 5 Data Engrams. This can be set to 0 to prevent NeuShield Data Sentinel from creating more Data Engrams.
Maximum Data Engram File Size
You can specify the maximum size of a file that Data Engrams will be created for. Whatever this is set to will prevent NeuShield Data Sentinel from creating backup copies or revisions of files that are larger than this value. So, for instance if this is set to 512 MBs than NeuShield Data Sentinel will not create revisions of files larger than 512 MBs. Files can still be protected if they are larger than 512 MBs but no backup copies of the file will be created.
Maximum Protected File Size
By default, NeuShield Data Sentinel protects files up to 2 GBs. However, you can change this to allow files to be protected up to 512 GBs. Files are still protected even if Data Engrams are not being created for these files.
Overlay Commit Interval
NeuShield Data Sentinel periodically copies data from the overlay onto disk. This allows changes made to protected files to be permanently saved. By default, this is done every 24 hours, excluding weekends. However, you can change the frequency of this. Setting this to a smaller number can reduce the amount of lost data when reverting a folder but will give you less time to revert the data if hit by ransomware. Setting this to a larger number could mean more data loss but gives you more time to respond to a ransomware attack.
Protected Cloud Drives and User Folders
NeuShield Data Sentinel all the default user folders such as Documents, Desktop, Contacts, Music, Pictures, Saved Games, Videos and 3D Objects automatically. This protection is provided to all user’s profile of the same system and these protected folders cannot be removed. However, they can be disabled from the ‘Protected Cloud Drives and User Folders’ page.
Protected Custom Folders
NeuShield Data Sentinel all the default user folders such as Documents, Desktop, Contacts, Music, Pictures, Saved Games, Videos and 3D Objects automatically. However, you can add custom folders to protect from the ‘Protected Custom Folders’ page.
User Control Settings
In some cases, you may want to hide the notification tray icon or restrict NeuShield functions from your users. To do this you can log into the NeuShield Portal and go to the ‘Data Sentinel Settings’ panel. When the client is restricted it is unable to change any settings on the client, add or remove protected folders, revert folders or run the One-Click Restore. Individual clients can be temporarily set to unrestricted mode from the ‘My Protected Devices’ panel.
Advanced Settings
By default, NeuShield will automatically detect and use whatever proxy server the system is configured for. However, in some circumstances you may want NeuShield to use a specific proxy server.
Platforms Supported: Score: 9.0 out of 10
While they don’t support Macintosh, basically any PC that is able to run Windows 7, 8 or 10 is supported as well as Windows Server 2008 R2, 2012 (including R2), 2016 and 2019. All features are available on x86 and x64 systems. Make sure you always have the latest service packs and security updates installed.
NeuShield Data Sentinel offers extensive compatibility with most existing antivirus and endpoint security products. This allows you to run NeuShield alongside your existing security products to fortify your computer and protect important data.
We would love to see a version for Macintosh, as it increasingly becomes a popular platform and potential ransomware target.
Features: Score: 9.8 out of 10
This product is loaded with the most well thought out and comprehensive ransomware defense features we’ve ever seen. Two very unique features are Mirror Shielding and One-Click Restore. This could save your computer or an entire organization from ransomware and ransom worms that are not normally detected (zero-day) by traditional anti-virus and endpoint security solutions.
Key Features
Mirror Shielding – This patent pending technology makes an attacker believe they have access to a computer’s original data files, but they are in fact only seeing a mirror image of them.
Document Reversion — Reverting is useful for undoing changes to your files that you don’t want.
One-Click Restore – Restores operating system files and settings back to a known good state .
Cloud Drive Protection – Protects local cloud drive folders (OneDrive, Google Drive, Dropbox, etc.), allowing destroyed or corrupted data to be recovered quickly without an Internet connection.
Boot Protection – Protects the boot portion of a drive to prevent aggressive types of ransomware from writing to the boot record and taking over the boot process.
Mirror Shielding
When NeuShield Data Sentinel is installed it adds a barrier to the user’s protected files preventing them from direct changes. When an attack tries to modify a protected file, it gets redirected and the file modification is stored on an overlay, keeping the original file intact. Later, if the user wishes to go back to the original file, it’s done by simply deleting the data on the overlay. This process of deleting data on the overlay is called reverting changes, more of which below.
As described by the company, an example of this application would be to imagine at work you had an important meeting with several coworkers to draw up a business plan. The business plan would be sketched out on a whiteboard and take several days to complete, meaning it would be left overnight where others could access it. However, unless you wrote it with permanent marker, it would be quite easy for someone to come by and erase it or modify it. You could put a note on the whiteboard to tell everyone not to erase it, but people may miss the note or just ignore it.
One way you could protect the whiteboard would be to put a piece of glass over it. Anyone who tried to write over or erase it would only affect the glass, the whiteboard behind the glass would be protected. When you come back the next day you can just wipe off the glass and your business plan would remain intact.
In layman’s terms, that is how “Mirror Shielding” works, by protecting the underlying data with an impenetrable shield not subject to interference by ransomware attacks.
Document Reversion
Reverting is useful for undoing changes to your files the user doesn’t want. For instance, if a new document is accidentally saved over the top of an existing document, the user can go back to the original document. It is also useful in cybersecurity by allowing reversal of undesired changes that ransomware or other malware does. When ransomware tries to encrypt a protected file, the encrypted files are stored on an overlay, but the underlying files are never changed. The user can simply revert changes, which will delete the encrypted data, allowing access to the original, unencrypted files again.
This method of recovering files is also useful for performance. It is significantly faster to delete a file than to copy or restore a file, which is what a backup does. Because of this NeuShield Data Sentinel can recover data almost instantly, no matter how much data is being protected.
Since the overlay only stores file changes, which need to be written to the disk in any case, there is virtually no performance overhead on the actual disk. NeuShield Data Sentinel can protect files with virtually no impact to the computer’s overall performance.
One-Click Restore
This feature is both a convenience and potential time-saver in a ransomware scenario. There are many things that can cause a whole computer or even a single application to stop working. It could come from a Microsoft patch, a system setting change or the introduction of ransomware or other malware.
NeuShield’s One-Click Restore capabilities make it easy to undo changes to the system allowing fast access to the computer, applications, and data. In addition to restoring the system back to a known good state, it recovers encrypted and corrupted operating system files, and removes known and unknown threats.
This new technology can take a snapshot of any Windows Server or Desktop operating system and allow network administrators to revert back to any snapshot. (Note—We are advised that Microsoft itself does not fully support System Restore on Windows Servers)
Cloud Drive Protection
With cloud drives, local files in a specified folder are synchronized with the cloud. This can be a problem because if a local file is encrypted or damaged, the damaged file is sent to the cloud and shared with all other devices connected to the cloud drive.
Whether a protected file is on OneDrive, Google Drive, Dropbox, or Box.com, Data Sentinel can recover files that have been corrupted or destroyed. NeuShield allows quick recovery of lost or corrupted data from the cloud drive, with a single click, and regardless of the internet speed available. With the offline recovery feature, NeuShield recovers data from the cloud drive even when offline or not connected to the Internet
Boot Protection
Protects the boot portion of a drive to prevent aggressive types of ransomware from writing to the boot record and taking over the boot process. The first layer of defense that Data Sentinel offers is boot protection. This protection will monitor the boot portion of your drive to prevent aggressive types of ransomware, such as Bad Rabbit, Satana, or MBR-ONI “Night of the Devil”, from overwriting the boot record (MBR) and leaving the device unable to boot. NeuShield Data Sentinel blocks applications from writing to the boot record without affecting normal Windows functions.
Three Coordinated Aspects of the NeuShield Data Sentinel Approach To Cybersecurity
Over the past few years many endpoint security products have come into the market, each claiming to meet your security needs. However, ransomware protection applications typically utilize only three ways to protect a device. Some products use only one of these techniques while other products use two or even all three of these techniques. NeuShield’s Data Sentinel employs all three, in unique ways.
Detection and Blocking
The first way that these products protect the user is through detection. They may use different techniques, such as signatures, machine learning, heuristics, behavior analysis, or other means to detect the ransomware and then block it. Detecting and blocking ransomware is the typical way that antivirus software works. This is very effective for known ransomware and other malware types. However Fully UnDetectable (FUD) ransomware cannot be blocked with these solutions.
It’s important to realize that ransomware authors routinely check their ransomware against various online services to ensure that their ransomware cannot be detected by existing solutions before releasing them into the wild. Relying on detection alone is not an adequate way to protect your device from ransomware.
Backing Up Files
Another technique that some anti-ransomware solutions use is to back up files to another location on disk before they are modified. This way once ransomware is detected they can revert these files back to a pre-encrypted state. Backing up files may work well for typical ransomware,but there are usually several problems with this approach.
First, backing up files doubles the disk activity (I/O) because each file that is modified needs to be backed up one-by-one, meaning it causes a reduction in performance. Secondly, many ransomware programs start out by attempting to delete all backups before encrypting the original file. In this case there is no way to recover since the backup has been destroyed. Finally, more advanced ransomware programs, such as NotPetya and Shamoon, do full disk encryption or simply wipe the disk of all data. For these cases backing up the files won’t help since the disk itself, including the backup, is overwritten.
Protecting Specific Folders
A third approach that ransomware solutions take is to block unknown programs from writing to protected folders so that only approved applications have access to these folders. This way ransomware would be blocked from encrypting files in protected folders.
At first glance this sounds like a good approach. However, enabling a feature like this can be problematic since it is difficult for users to determine which applications need to be approved. For managed environments this can result in complaints from users who have different third-party applications that need specific access to these folders. Also, a potentially worse problem is that allowing an application, even a known good application, may open a backdoor to allow ransomware in. Ransomware can use these approved applications to encrypt data. For example, there are ransomware programs that use Microsoft Word macros to encrypt files. In addition, just like backing up files, this does not help against ransomware that encrypts or wipes the full disk of all data. Controlling access to folders by itself does not fully protect against ransomware.
Customer Support and Documentation: Score: 9.4 out of 10
NeuShield does not yet offer a telephone support line. They do offer comprehensive online knowledgebase and documentation currently hosted at: https://support.neushield.com/hc/en-us. You can create a ‘trouble ticket’ or support request at this portal, once you’ve signed up. While they did a great job with documentation, we’d give them a 10 out of 10 if they offered standard telephone support and paid extended hours support.
Pricing: Score: 9.5 out of 10
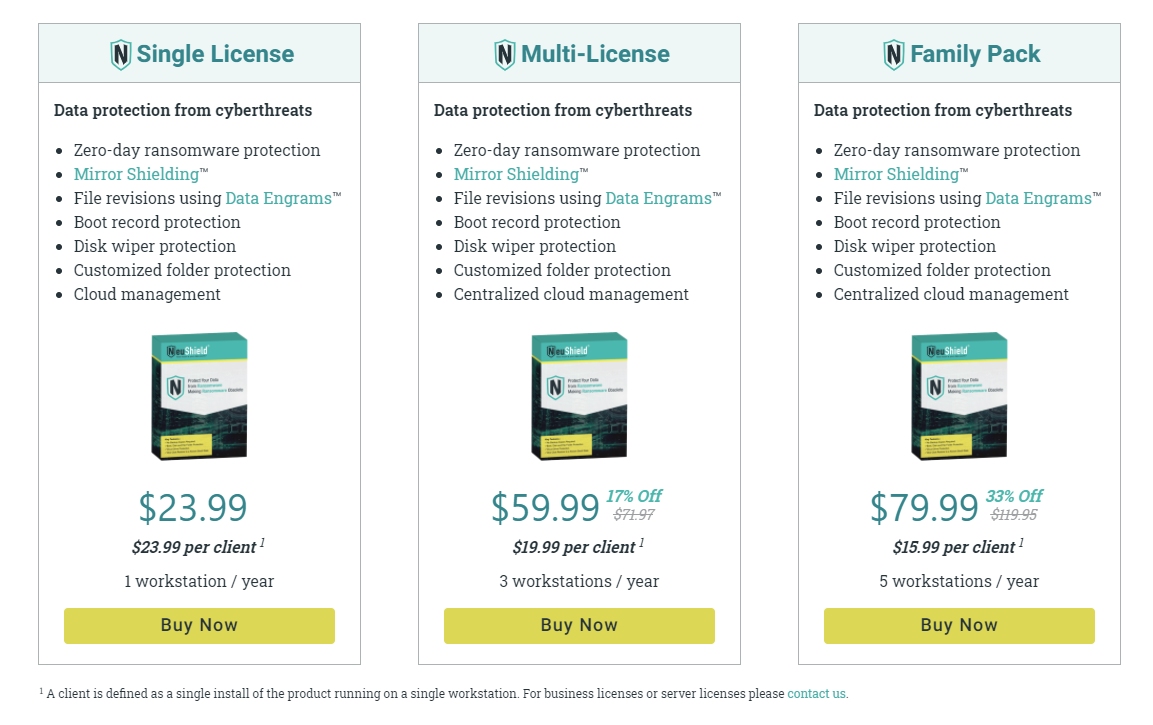
For 1 endpoint to 5, their Home software edition ranges from $23.99 to $79.99 USD. This is very consistent with market rates for other major brands of Antivirus software – and remember – you’re getting Zero-day ransomware protection not discovered by most anti-virus products, file, boot and disk protection. We haven’t seen coupon codes or discounts and if they reduced the price by $4-6 and offered frequent special discounts, we’d give them a 10 out of 10 on pricing.
Final Thoughts
NeuShield is a must have in your endpoint security portfolio.
NeuShield stands out because it is one of the only products that does not rely on detection and blocking. Instead, the Data Sentinel controls how the hard drive is accessed, allowing customers to recover from ransomware even when the ransomware cannot be detected.
NeuShield Data Sentinel takes a completely different approach by creating a protective shield between the user’s files and applications. When ransomware or other application tries to make changes, the original files stay intact allowing users to revert any unwanted change that has been made.
While other products create backup copies of your files which, can dramatically increase disk usage and cause a significant performance overhead, NeuShield’s revolutionary Mirror Shielding™ technology can preserve the original file without requiring a backup. This allows Data Sentinel to protect files with virtually no additional disk activity (I/O).
In addition, the boot portion (MBR) of the user’s drive is monitored to prevent aggressive types of ransomware and disk wiper malware from overwriting the boot record or leaving the device unable to boot. Raw disk access is also monitored to prevent wipers and malicious ransomware programs from destroying or encrypting drives.
For its small footprint, ability to augment any existing antivirus product, ease of use, solid documentation and powerful features, knowing that ransomware is on the rise and getting even harder to detect, we consider NeuShield Data Sentinel a must-buy product.
Overall Review Score: 9.7 out of 10
Visit NeuShield online, today: https://www.neushield.com/