by Tarun Desikan, COO & Co-founder, Banyan Security
Upendra Mardikar, CSO of Snap Finance discusses how to modernize infrastructure access and implement zero trust security.
Tell me about Snap Finance. How did the pandemic quarantine affect security for your company?
Snap Finance is a mid-size FinTech company with about 1500 employees and contractors. We develop products for retailers who want to offer lease-to-own, buy-now-pay-later and we also offer lending services direct to consumers. We are primarily focused on the U.S. and U.K. markets. The nature of our products means that our customers are generally for credit challenged consumers, known as ALICE: Asset-limited, income-constrained, yet employed customers. Our products are disrupting financial services and making life easier for ALICE customers. Treating these customers with trust, respect, and dignity that creates a long-term, lasting relationship is extremely important to us.
We have offices in multiple locations in the U.S., Costa Rica, and the U.K. When the pandemic hit us, shelter-in-place orders forced the company to immediately move to work remotely. Policies and budgets were changing rapidly. This was not unique to Snap Finance. All of us had to adapt to this new world. Even now, we are still working remotely with a few exceptions.
To the viral pandemic, industry is seeing unprecedented security challenges arise, including what some were calling the cyber-pandemic – high profile attacks happening frequently to enterprises across the globe.
At Snap Finance, we take the security of our customers very seriously. In this new era, we needed to continue our journey of expanding our security posture.
What are the drivers that led you to Zero Trust?
We had multiple drivers. Once we realized that we had to support all our employees working 100 percent from home, we encountered three main challenges:
- Home networks. Our customer care/call center all had to work from home. These folks deal with sensitive financial information, especially with the lending products, so home networks had to be at enterprise-level security. Of course, we have to ensure this happens while keeping our employees’ privacy in mind. They could have IOT devices, they could be using default passwords, etc. We don’t know. That was the first issue.
- Cloud services. Snap Finance is a Digital First Cloud-Native technology organization. All our services are on cloud. In addition, we use multiple cloud service providers and we have to enable access to these services securely. In addition to Office 365 we had cloud services for our CRM, our HR system, our expense management system, etc. Securing these services and keeping them behind VPN wasn’t the best architecture.
- User experience and performance. We needed to make sure the user experience didn’t hinder productivity. We don’t want employees to have to remember a hundred different passwords, or use multi-factor authentication (MFA) every login to a hundred different services. We wanted to make the transition to working from home as seamless as possible.
Can you describe the other security measures you were using in addition to Zero Trust to secure working from home?
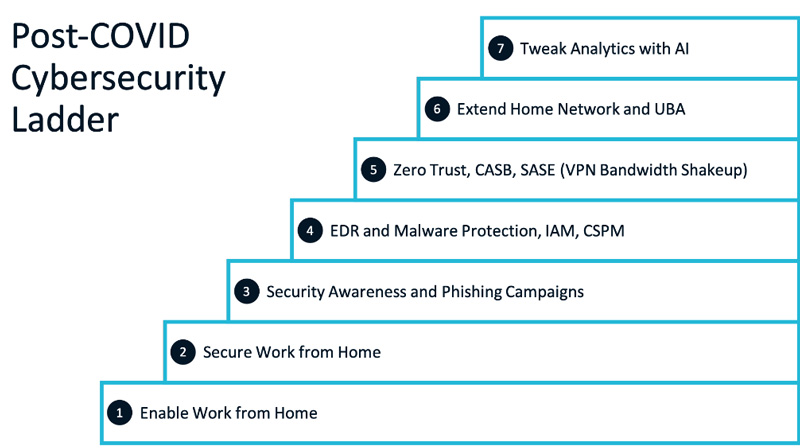
Once COVID hit, we worked our way up a ladder of security measures that included Zero Trust. There were seven steps:
- First, we had to enable work from home. We had no choice. We previously used VPN, but had scalability and performance issues. Our employees had to log into multiple data centers, we had VPNs at multiple instances. U.K. employees had to log into one VPN, West Coast employees had to go to another location, etc. It was not ideal.
- Once everyone was working from home we did threat modeling. One of the primary threats was insecure modems and home networks so we helped all our employees secure those networks and started employee training and security awareness to lower the risk.
- We monitored news all around and noticed that industry saw 30,000% increase in phishing! With phishing, the hardest part to control is the “human factor”. You can put a lot of technology measures in place, but stopping humans from clicking that link is key.
- Cybersecurity posture management. This is where we added malware protection, endpoint detection and response (EDR), and identity and access management (IAM).
- Zero Trust Network Access (ZTNA) became super popular in our company when people realized we could do away with the VPN and its multi-factor authentication. We could offer employees a “boom, you’re connected” experience. It was a hit with our users because of the experience. People had been frustrated by the friction they were feeling every time they needed network access. Our experience with ZTNA has been very positive.
- Extend home networks and UBA. Once we implemented Zero Trust, that allowed us to worry less about employee home networks and we could move our efforts to adding in user behavior analytics (UBA) for an additional security layer.
- AI. Our AI implementation is the last layer of security for us and it’s one we’re still tweaking and implementing. But we couldn’t have gotten this far without the previous levels.
According to a recent Microsoft Zero Trust adoption survey, 31 percent of respondents said preparing for a hybrid workplace driven by COVID-19 was a top motivator for adopting Zero Trust Network Access. Do you think COVID actually improved the overall security of your organization? Would you have done all this work without the pandemic?
COVID has certainly accelerated it. We would have implemented Zero Trust Network Access either way, because the trends pushing us in that direction already existed: we had a distributed workforce, we were using cloud services, experiencing performance issues, and our employees had a lot of friction when trying to get network access. We have a lot of salespeople and when they had to VPN from the road every time they made a sale it was not a great experience. Now that things have moved to a much more open, remote work environment we definitely need this type of solution for remote access.
Based on our experience, Zero Trust Network Access is the way to go for any organization.
How is a VPN different from Zero Trust Network Access (ZTNA)? How does it work with Azure AD?
The goal of both VPN and ZTNA is to make sure that the devices that are connecting to your network are the right devices.
One difference is in the user experience. With a VPN, when users open their laptop away from the office, they have to launch the VPN client and log into the corporate network. It creates a secure tunnel to the corporate network. ZTNA on the other hand, authenticates users and devices and knows that the resources you are connecting to are trusted and secure. With ZTNA we have confidence that every device is supposed to be connected and that they are not compromised. This even works for SaaS applications. With VPNs you either connect directly to the SaaS resource without security, or you have to log into the VPN, go to the corporate network, then send the request to access the SaaS. Zero Trust eliminates that circular route.
The VPN places trust in the network. ZTNA doesn’t make any assumptions about the network, but instead makes sure the device and the user are trusted, and that every single access is explicitly authorized and authenticated. For example, if a user tries to connect to a server, that request is granted only if a central command center has authorized that connection.
Our ZTNA solution, Banyan Security, is integrated with Azure AD, so access to all private resources is tied to user credentials in Azure AD and device trust via the Banyan App. Users access our internal applications and infrastructure just as they would SaaS applications like Office 365 and Salesforce. Using Banyan for infrastructure access allows us to limit access to just those specific applications and services rather than giving access to an entire network. This reduces the size of the attack surface.
What are the benefits of ZTNA?
ZTNA gives users the benefit of one-click access to internal resources, without the hassle of needing to turn on the VPN. It gives us device and user trust-based access control versus simply trusting anything that gets access to the network. It also scales much better than any VPN, quickly and conveniently, especially integrated with a cloud platform like Microsoft Azure AD. Finally, we also like that access is only granted with short-lived credentials and policy is continually enforced, so if something changes to make the user or device a higher risk, access is revoked.
What is one challenge most companies don’t anticipate in the migration to ZTNA?
It’s hard to anticipate the number of users, devices and applications you’ll need to include in your project before you start deploying. So getting visibility into your environment and taking an inventory of all your applications becomes key. And that can quickly become overwhelming unless you invest in a ZTNA solution with strong visibility capabilities.
In a software-driven organization, IT often doesn’t know every application the company’s developers are using or creating in-house, so the discovery problem is not a one-time issue but an on-going problem.
I recommend taking the process in stages. Start with what you know. Roll out to a small group of users and applications. Enforce basic policies first. And then build from there.
About the Author
Tarun Desikan is the COO & Co-founder of Banyan Security. He has extensive experience in product strategy and business execution from nimble startups to global corporations. He was most recently VP of Product at Moovweb, where he helped build a leading PaaS for mobile development, migrating 100s of enterprises to modern infrastructure in the Public Cloud. Prior to Moovweb, he was a strategy consultant at the BCG focused on marketing & sales initiatives for Global-1000 IT companies. Tarun was also an early engineer at Infinera (Nasdaq: INFN), developing networking products. Tarun holds a BS in Electrical Engineering from BITS, Pilani, India, and an MSEE and MBA from Stanford University. Tarun can be reached online and at our company website https://www.banyansecurity.io.


