We are taught never to lie, but if one opponent uses it, then deception becomes required by the other in order to win
by Carolyn Crandall, Chief Deception Officer, Attivo Networks
From childhood, we were taught never to lie. Deception is bad and cheaters never win.But what happens when your opponent is blatantly using deception to tip the odds in their favor? At what point must you adapt to level the playing field and have a fighting chance at beating your opponent? Barton Whaley once wrote that “In combat, deception can strengthen the weaker side. Moreover, when all other factors are equal, the more deceptive player or team will always win.” This situation is the epitome of reality when applied in the world of cyber warfare. Cybercriminals use deception to trick users into clicking on phishing emails, accidentally downloading malware, and inadvertently sharing login credentials. They also use tactics to keep their presence hidden below the noise level so that they can continue to quietly escalate their attacks.On the other hand, cyber defenders have tried to win the game by pursuing these adversaries by looking at behaviors and logs to assess anomalous behavior. Essentially, they are reacting to actions taken, learning from them, and then pursuing their opponent with the intelligence and forensic evidence they can gather. It is a time-intensive process that also requires the security team to have to cull through and correlate attack information, which in many cases can also be infused with false-positive data.
Here is where the playing field can get leveled with deception technology. It is based fundamentally on ambushing the attacker as opposed to pursing them. As an attacker attacks, they fundamentally believe that everything that they see is real. Some of the most fundamental tactics used within cyber deception are to create decoys that appear as production assets. These fakes, which can appear as endpoints, servers, network infrastructure, IoT, and ICS-SCADA devises or as a variety of cloud functions, databases, and containers are designed for believability and appear as attractive targets for an attacker. These network decoys are powerful for detecting lateral movement based on scans and attacker reconnaissance early. They also do this in a way that is easy to deploy, operate, and manage. Given that there is no employee production value to these devices, any touch to a decoy delivers a high-fidelity alert that notifies the defender that something is happening that needs immediate attention.
Credential theft is another primary attack vector and is used by actors seeking to escalate privileges so they can access their targets. There are many creative ways for tricking and derailing attackers interested in credential harvesting. Organizations can use machine-learning to not only create decoys but to also create credentials and lures that appear like an actual user’s or admin’s. These lures then work to breadcrumb the attacker away from the production environment into the decoys where they can be studied and better understood.
Going system by system to find the credentials of value can be a slow process, however most attackers will head straight for an Active Directory Server to get the information they are seeking on users, admin and privileged accounts. Often referred to as the phone book or GPS of the network, compromising AD can save an attacker a significant amount of time if they can successfully crack it. Deception plays two roles in faking out attackers seeking to enumerate AD. The first is in being able to create decoys that entice the adversary to engage and the second is a new technology that detects unauthorized queries and changes the response so that the attacker receives only fake information that is designed to misdirect their attacks into decoys. Lying to attackers in this way is quite impactful in that an attacker’s automated tools will be tricked andan attacker will no longer be able to rely on them. This will dramatically slow their ability to attack and increase their costs. Both of which can be helpful deterrents. I particularly like this form of deception because of its efficacy in detecting unauthorized activities and because infosec teams get notified well before the situation turns into a live attack. I also like that this can be done without touching the production AD environment, which is a shortfall of other AD security controls.
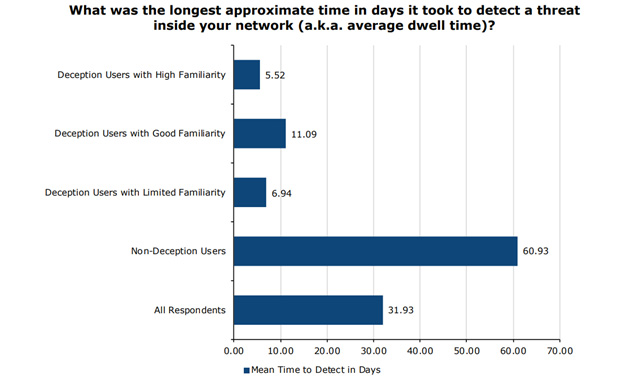
A modern deception platform will continue to add value in a myriad of other ways, which can include fake mapped drives for derailing ransomware attacks. For platforms that are high interaction, you can also activate features that will occupy the attacker by feeding them reems of data to encrypt. This provides not only an early alert but also contains the spread of the attack. Advanced platforms will also have integrations built in that automate isolation, blocking, and threat hunting. Altogether, the accurate detection and response can reduce dwell times by up to 90 % and response times by a factor of 12.
Decoy documents also play a useful role in determining what an attacker is after and in protecting real information. By embedding fake documents within the environment, an attacker believes they have succeeded in their heist and organizations can get insight into what both external and internal threat actors are seeking. This can be incredibly insightful for IP, research, and case file theft that can often go undetected. Geolocation services can also be applied to determine if a document is opened within the company or externally.
Throughout all of this, you will see that the use of deception is centered on defending your organization from attackers that are within your network already. Note, that I am not advocating for the use of deception to hack back a cybercriminal. Although it may feel tempting, it is illegal and could be quite dangerous to those that are not equipped to do so. Some of the perils include identifying the wrong opponent, harming the innocent, disrupting and investigation, or simply making yourself an increased target. By staying focused on in-network detection you are within the same rights to protect yourself with deception as you would be with other security controls.
Organizations both small and large and those with mature and immature security operations are gaining vast benefits in using deception to quickly detect in-network threats. Many, however, will want to go beyond detection and will want to use the ability to safely engage an attacker in a deception environment as a way to gather company centric threat intelligence. Those seeking this additional information will find that they can efficiently gather the TTPs and IOCs of an attack and that by using the automated attack correlation and incident response automations that they can decrease response times from hours to minutes. Many will also activate deception platform capabilities that include being able to map attack paths based on exposed credentials and other visibility tools for insight into network adds and changes that create risk.
Although calculating security ROI is challenging, in the case of deception, the reduction of dwell time, triage, and response time can be calculated in tangible time savings and in removing unsubstantiated alerts from the equation. Others will look at deception as a force-multiplier to other investments such as EDR, SEIM, and SOAR. In each of these cases, deception closes detection gaps, but also given the fidelity of alerts, will provide attack data that can automatically be sent and activated within these other platforms, saving organizations valuable response time.
Cyber attackers have subscribed to the saying “It’s all fair in love and war.” With deception now being used by defenders, the playing field is definitely fairer, and we have the homefield advantage that we can leverage to further tip the odds in the defender’s favor.
About the Author
Carolyn holds the roles of Chief Deception Officer and CMO at Attivo Networks. She is a high-impact technology executive with over 30 years of experience in building new markets and successful enterprise infrastructure companies. She has a demonstrated track record of effectively taking companies from pre-IPO through to multi-billion-dollar sales and has held leadership positions at Cisco, Juniper Networks, Nimble Storage, Riverbed, and Seagate. Carolyn is recognized as a global thought leader in technology trends and for building strategies that connect technology with customers to solve difficult operations, digitalization, and security challenges. Her current focus is on breach risk mitigation by teaching organizations how to shift from a prevention-based cybersecurity infrastructure to one of an active security defense based on the adoption of deception technology.
“If you travel a path that is already well traveled, you won’t likely discover anything new. Be curious, take chances, and remember we are never lost, just exploring”
Carolyn is an active evangelist, blogger, byline contributor, and speaker on industry trends and security innovation. She has spoken at industry events around the world, has been a guest on Fox News, has been profiled by the San Jose Mercury News, and has received many industry recognitions including Top 25 Women in Cybersecurity 2019 by Cyber Defense Magazine, Reboot Leadership Honoree (CIO/C-Suite) 2018 by SC Media, Marketing Hall of Femme Honoree 2018 by DMN, Business Woman of the Year 2018 by CEO Today Magazine, Cyber Security Marketer of the Year 2020 by CyberDojo (RSA), and for 9 years a Power Woman by Everything Channel (CRN). Additionally, Carolyn serves as an Advisory Board Member for the Santa Clara University Executive MBA program and co-authored the book Deception-based Threat Detection, Shifting Power to the Defenders.
Carolyn Crandall can be reached online at ([email protected], Twitter: @ctcrandall, LinkedIn: Carolyn Crandall) and at our company website https://www.attivonetworks.com


