Our cars are becoming smarter, more comfortable and safer. At the same time, advanced technology quietly introduces new risks, which are unknown to consumers and problematic for vendors. Let’s explore the “dark side” of smart cars.
Aleksander Gorkowienko, Managing Consultant, Spirent Communications
Close your eyes for a minute and picture yourself driving your new, modern car down the highway on a glorious sunny day. You bought the car last week and now have that “life is so good” feeling. You sit comfortably, driving 70 mph with cruise control on, enjoying how robust, strong (and not to mention smart) your new car is. But then you notice the radio station changed and the volume increased autonomously and you can’t turn it off. Then things stop working the way they should and your dashboard flashes like a Christmas tree. What once was a blissful joyride quickly turned to an alarming situation. Your car was hacked by an unknown attacker, who does not know you, and who has nothing personal against you. He simply ran a sequence of exploits against a random car in the vendor’s network for fun, because he can. And for you? For you, it means a seriously unlucky day.
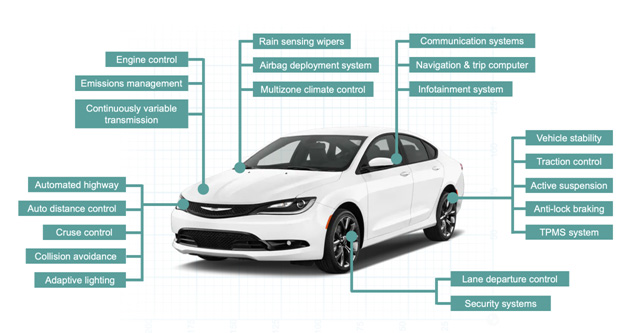
Many existing cars could also be called “smart,” without a doubt. Modern vehicles are packed with advanced electronics and, with confidence, we can call it “IoT on four wheels.” We are witnessing a radical reimagining of the automobile. Car remote control, biometric sensors, reading road markings and signs, active cruise control and even augmented reality are being used more and more. Those features become ubiquitous because modern vehicles are a good example of something that in the aviation industry is called “fly by wire.” There is no direct connection anymore between the controlling elements, such as the driving wheel and pedals, and the car wheels and engine. The former ones are simply an interface from the human to the central computer which is steering the car.
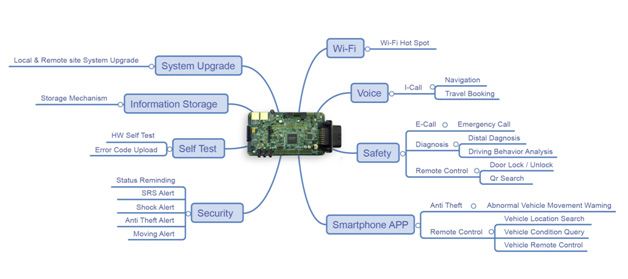
This is not a new concept and has been quite reliable in general (well, all airplanes in the world are built with it), but now we have an additional element that dramatically changes the dynamic. The computer in the car can always be connected to the network and multiple cloud services provided by the vendor. Vehicles are already equipped, or will be mandatorily equipped very soon, with a device called T-box. T-box is a connected-car terminal that delivers multiple online applications, including vehicle remote monitoring, remote control, safety checking and remote diagnosis via remote wireless communication. Such a device already has embedded GPS satellite positioning, its own acceleration sensing and can have direct communication lines with the other car components over the Intra-vehicle network. This means that if there is a flaw in the car design and the T-box can be accidentally reached by hackers, they would have full access to your car and their actions will be limited only by their imagination.
One may ask: how on earth do hackers gain access to my car through the vendor’s wireless network? You might be surprised how easy it can be. And, as usual, the first problem is that the automotive vendors simply do not expect that someone would ever try to do that. With that mentality, they are very mistaken. Various telemetry components of existing connected cars could be either bought on eBay or scrapped from the local junkyard. Those telemetry Electronic Control Units (ECUs) can have an embedded SIM card and a 4G modem. Once you know how to power on and communicate with such ECU on your workbench, you can connect to the whole vendor’s automotive cloud. At that point, your security depends on the vendor. Some of them, indeed, have good protection in place but others might have all the connected cars in one massive flat network. Once hackers reach such a network, they can scan it, discover active IP addresses, identify open ports, etc. Each discovered IP address means a connected car. If the hacker randomly picks an IP address associated with your car and exploits it – well, the story can be similar to what was described earlier.
Furthermore, in budget automobiles, some premium features could be locked by default until you pay for them (or are available only to service personnel). It does not come as a surprise that there is a flourishing market of “tweaked” third-party firmware for cars where those features are magically enabled. Alternatively, you can buy unlicensed (and, naturally, inexpensive) tools which can be used to reconfigure software in your car. Such firmware can have malware or spyware embedded, meticulously collecting sensitive information about you, such as your phone calls, the content of your phone book, history of your calls, the music you like to listen to, and when and where you drive The attacker can even learn your driving habits, such as the way you accelerate and use brakes. All this information can be used against you or sold on the Darknet. Probably not immediately, but in months when this behavior does not look suspicious. Considering the risks outlined, one should be extremely careful with any kind of “digital DIY” with modern cars. This is similar to illegal Android firmware and software – yes, you can find and download it for free, but the consequences of installing such software, or rather malware, on your smartphone can be very dangerous. It took a few years for mobile phone users to learn from their mistakes and, sadly, smart car users seem to be following the same pattern now.
Gartner estimated that this year, a quarter of a billion connected vehicles will be on our roads, becoming a major part of the global Internet of Things. Statistics show that 79.86% of passenger cars sold in 2020 are already in some way connected and that by 2022, the market penetration will be even higher. Automotive technology is expanding immensely, but even so, security in modern vehicles is an equivalent to that of computers from the ’80s, when encryption, protection of sensitive data and identity were at their infancy. Every new “cool” wireless feature added to a car is creating another entry point for hackers. Privacy within the connected car no longer just means tinted windows.
So, how can we, as car owners, make our cars safer? Here are a few tips:
- Reduce the attack surface. Switch off all unnecessary or rarely used wireless functionalities in your car. If you really cannot live without having WiFi in your car, make sure to use a strong password.
- Unless you are a security professional (and you really know what you are doing) do not ever try to “jailbreak” or “root” your car or install any unlicensed firmware or software. It’s not only about voiding your warranty, it puts your life at risk.
- Always update firmware for your car once it has been issued. Updates are issued for a good reason, and many times for security reasons. Contact a car dealer or your mechanic and make sure the car’s firmware is up to date.
- Do not use any “tweaked” or third party applications to control your car. You do not know what is inside. Phone apps could be a serious threat to both your security and privacy.
- Do not plug random devices into the car’s USB ports or OBD2 diagnostic port. (The one often located under the dashboard and used by mechanics). Be very cautious with devices like the dongles supplied by auto insurance companies, which collect information on your driving habits and share over the internet.
Automotive vendors should understand that well-thought out security features could be the key for quick adoption of the new technologies. Entities at all levels, such as OEMs, dealerships, service providers, governments and consumers must be aware that security in modern smart systems is not a binary “secure or insecure.” Rather, security is a continuous process of assessment, optimization and re-evaluation again and again. A weighted balance and sensible approach is a golden rule that works well, and will work for smart cars as well.
About the Author
Aleksander Gorkowienko is a cybersecurity advocate, trainer and speaker with more than 20 years of practice in the security business, working in numerous industry sectors. He is a senior consultant and a part of the vibrant Spirent SecurityLabs team. Aleksander has a passion for cybersecurity which he shares with business leaders and industry audiences both through his work as a security professional and through his various public speaking engagements. His primary focus is ethical hacking and building corporate cyber resilience. Aleksander is a practitioner, managing penetration testing team for years and helping companies and individuals to protect their valuable assets and data. He believes that cybersecurity is never a one-time action – it is a continuous process which engages the whole organization on all levels and requires all employees to be aware and confident of modern cyber threats.
More information about Aleksander and Spirent Communications: https://www.spirent.com/solutions/cybersecurity


