By Alban Diquet, Head of Engineering, Data Theorem
Many countries are easing “stay at home” restrictions imposed to combat the novel coronavirus. Government and health leaders are looking for ways to conduct mass-scale contact tracing to prevent a resurgence of the virus. With no vaccine available in the near term, contact tracing is one way to ease quarantine restrictions but still have a way to identify people who interact with others who might be infectious. However, certain API security measures should be taken to ensure data protection and user privacy.
One thing we know about the coronavirus is that people in close contact with someone who is infected are at higher risk of becoming infected themselves, and of potentially further infecting others. Contact tracing attempts to identify and then closely watch these contacts after exposure to an infected person in order to help them get appropriate care and to prevent further transmission of the virus.
Contact tracing isn’t tied to any particular approach or technology. However, with billions of people worldwide at risk from virus exposure, technology and security need to play a role in the process. Traditional methods of manual tracing can’t scale to meet the enormous need.
Smartphone Apps Enable Automatic Contact Tracing
One tracing strategy is the use of smartphone apps to continuously log the user’s location and notify them if they’ve recently spent significant time near someone who later tests positive. Every app user’s location data is sent to an authorized agency such as a national health authority. The “tracing” is done server-side by analyzing the location data, which is cross-referenced with supplemental data such as credit card records, security camera footage, and so on. If the app user is at risk due to potential virus exposure, they receive a push notification to get tested or self-isolate at home.
Applications that track people movements – often with invasive data collection – are already in use in China and South Korea. Other types of apps are being tested as well. In Australia, more than 2 million people downloaded a government-sponsored app in a matter of days. A coronavirus-tracing app in India became the fastest-ever app to reach 50 million users.
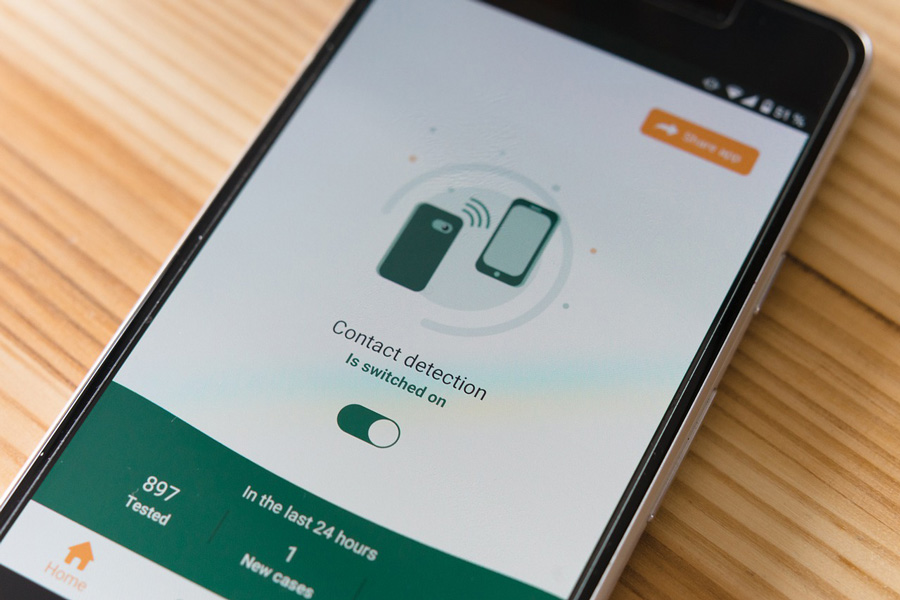
There are various means of using smartphone-based technology for contact tracing. One uses location data provided by the cellular network. Another less invasive method utilizes Bluetooth communication.
Apple and Google Collaborate on Contact Tracing
Apple and Google are collaborating on an application coming this month on both the iOS and Android platforms. With this app, the user’s phone scans frequently for nearby devices via Bluetooth and stores a privacy-preserving “Bluetooth ID” of every device encountered. Users with a positive COVID-19 diagnosis can send a privacy-preserving “Device ID” via the application to a centralized server.
All users regularly download the list of Device IDs of infected persons from the central server. Their app then compares this list of infected users’ Device IDs with the list of Bluetooth IDs of devices that were near them in the past. If a user has been in contact with an infected person, they get an alert on their device.
Apple and Google claim to have addressed the privacy issue. Device IDs and Bluetooth IDs can be compared using a privacy-preserving mechanism that doesn’t disclose user identities. Moreover, the alert is not sent to the server to protect users’ identities.
The two tech companies have outlined several important privacy goals:
- The server never has access to users’ location data
- The server never has access to who was in contact with whom
- Users only willingly share the fact that they have tested as positive for the virus
Other Approaches to Contact Tracing
Singapore implemented a program similar to the Apple/Google proposal. It uses Bluetooth to detect contacts. Individuals can decide whether to share information with the government. No location data is ever collected or sent to the central server.
Europe’s approach is known as Pan European Privacy-Preserving Proximity Tracing (PEPP-PT). PEPP-PT is an organization with more than 130 members consisting of scientists, technologists, and experts from international research institutions and companies. Similar to the Apple/Google proposal, PEPP-PT’s approach adheres to strong European privacy and data protection laws and principles.
The United States has multiple efforts underway.
Stanford University is developing COVID Watch in collaboration with other teams around the world. Stanford’s researchers discovered a way to build an anonymous exposure notification system which never collects identifying information. The app checks for other apps in proximity using Bluetooth and anonymously notifies users if they had contact with someone later confirmed to have COVID-19.
One of Stanford’s collaborators is CoEpi: Community Epidemiology in Action. CoEpi is a privacy-first system for anonymous Bluetooth proximity-based exposure alerting based on voluntary symptom sharing. Communities of close contacts install the app and self-report virus symptoms. Users who then interact can create an early warning system to detect and respond to any infectious disease.
MIT has developed Private Kit: Safe Paths, in which an infected person opts to provide a 28-day location trail to their health official. Using the web app Safe Paths, the health official redacts personally identifiable information from the location trail to anonymize the infected individual. The patient’s location trail is released. Private Kit: Safe Paths notifies users who came in close contact with a diagnosed patient. Healthy users never surrender their private data to anyone.
The above efforts utilize Bluetooth technology to determine proximity to infected persons. There are, however, low-tech methods for contact tracing. The city of San Francisco is going low-tech due to concerns about privacy and civil liberties. The city’s effort doesn’t involve a smartphone tracking app, but rather old-fashioned phone call interviews with patients who tested positive.
Safety First
There are many unknows regarding COVID-19. The world is scrambling to address fear, precautions, and getting back to a new “normal.” These contact tracing methods sound like they hold some measure of promise and data protection, but they are understandably new and untested.
What we do know is that data protection and user privacy are critical with these apps and contact tracing methods. Hackers are ingenious and opportunistic, we know if there are ways to exploit these APIs and tracing techniques, cyber criminals will find them.
While specifics of these APIs and tracing techniques are coming to light, these APIs should have certain good-hygiene safeguards in place.
We know that API security must be a continuous process. It is not effective for these organizations and countries to roll out apps, check the APIs for malicious code content, add some privacy controls, and let them run their course. It is essential to monitor API security controls continuously, and automation is critical for effective continuous API analysis. A new approach today involves continuous follow up with dynamic, run-time analysis that can uncover real security problems in APIs. Done right, automated analysis identifies critical issues with a clear path to remediation.
Conclusion
Contact tracing is an important element to help societies return to some level of normalcy again. There are many approaches in use or under consideration, both high-tech and low-tech. Many of these approaches have the potential to expose sensitive information, including a user’s infection status, location data, and history of contacts. All sensitive information must be appropriately protected.
As for the high-tech methods, the Bluetooth approaches seem promising. Time will tell how effective they are in limiting the spread of the novel coronavirus. But if the data being collected is not secured and protected using these contact tracing methods, we may see a backlash against these high-tech approaches to control the spread.
About the Author
Alban Diquet is Head of Engineering and Chief Architect of Data Theorem. Alban’s research focuses on security protocols, data privacy, and mobile security with a focus on iOS, Android, and Windows Phone devices. Alban has released several open-source security tools including SSLyze, iOS-SSL-Kill-Switch, and Introspy. Furthermore, he has presented at various security conferences including Black Hat USA, Hack in the Box, and Ruxcon. Prior to joining Data Theorem , Alban was a Principal at iSEC Partners, Inc. Alban received a MS in Computer and Electrical Engineering from the Institut Superieur d’Electronique de Paris in Paris, France, and a MS in Secure and Dependable Computer Systems from Chalmers University, in Gothenburg, Sweden.
Contact: https://www.linkedin.com/in/adiquet