by Ken Carnesi, CEO, DNSFilter
The effects of COVID-19 can be felt in our daily lives, everything from individuals working-from-home to big businesses suddenly struggling. But the effect can also be felt in the cybersecurity space, where futures are just as uncertain.
What can we expect of the long-term effects the coronavirus will have on cybersecurity?
Large-scale panic is ripe for ransomware-as-a-service
No matter the disaster, cybercriminals will always be there to cash in. They deployed attacks during Hurricane Katrina and the Australia bushfires, and they are deploying attacks targeting coronavirus concerns in record numbers.
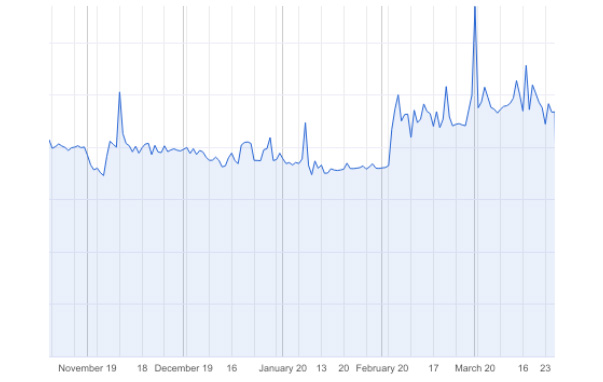
In the chart above, you can see a progression of “bad sites” that DNSFilter detected on a daily basis from November 2019 through March 2020. “Bad sites” refers to anything that’s categorized as malicious or deceptive and includes sites that host or link to malware, trojans, credential phishing sites, or use deceptive advertising practices. Our numbers reflect what you’ve been seeing in the news: malicious sites have significantly spiked in 2020, specifically around the time coronavirus became big news.
We’ve seen an 11% spike in threats detected beginning in February. The spike the week of March 1st? That’s the week the U.S. saw their first coronavirus-related deaths and companies started to move to a work-from-home atmosphere (more on that in a bit).
But it’s not just about more threats. Specifically, we expect to see more ransomware-as-a-service (RaaS) attacks because of coronavirus.
RaaS is SaaS’ evil twin. Essentially, it’s a business model where vendors provide malware to “customers” who can then deploy it. The ideal customers of RaaS is someone with little technical knowledge who wants to hit people where it hurts. These might be scam artists or even those in organized crime.
And if you look at coronavirus through the lense of a criminal: The situation is ripe for exploitation. This event is unprecedented because everyone in the world has one thing on their mind. It’s a rare moment that hackers have on their hands. It enables RaaS providers to put together coronavirus packages, similar to do-good companies like Zoom offering their services for free.
Healthcare cybersecurity will take a hit
When we talk about RaaS, no industry is at a greater risk right now than healthcare.
Our healthcare systems worldwide are overwhelmed, and because healthcare workers need their IT systems up and running more than ever, they’re the ones most likely to pay the ransom.
However, the risk isn’t just ransomware. It’s also just the continued use of strained, legacy systems.
Healthcare systems are overloaded. Applications are in the cloud. The risk of accidental insider leaks has increased tremendously because of coronavirus.
With budgets directed toward personnel and supplies right now, expect hospital IT teams to be as budget conscious (or moreso) as the rest of the world.
Hospitals that don’t already have sophisticated cybersecurity measures in place will need to wait it out until the pandemic dies down. And they’re not alone.
Companies will switch to barebones security at their peril
Some companies are going to be like a sinking ship: throwing everything overboard that might be weighing them down. For some IT teams, that’s going to result in tools that are deemed “nonessential” getting cut.
Barebone IT won’t become the standard, by any means, but we will start to see companies panicking and moving in that direction.
This isn’t necessarily the route that companies should go, as with each tool they cut, they’re exposing themselves to more cybersecurity risks at a time when cybercriminals are hyperactive. However, companies that don’t view cybersecurity as a major necessity because of lack of education and training will be making this decision.
Businesses will be focused on staying afloat amidst this crisis, and they won’t be considering the ramifications of their actions likely until it’s too late. This will most likely affect small local businesses as opposed to large corporations or even mid-sized companies.
Cybersecurity vendors need to brace themselves for these hard conversations and emphasize the importance of having security in place.This is the time that businesses need more security, not less.

Cybersecurity vendors need to accommodate working from home
You’ve probably heard enough about working from home being the new normal forever, but it doesn’t change the fact that this is changing everything.
What working from home is really demonstrating is the lack of preparedness as a whole in cybersecurity for remote employees. While some cybersecurity vendors have addressed these issues, there are plenty who still have nothing in place. That means their businesses are hurting.
In order to thrive, cybersecurity vendors need to consider the work-from-home client and make accommodations to their product based on this. If they don’t, they’re likely to be hurt the most by what is clearly becoming a cash-strapped economy.
Which brings us to the last point.
Not all cybersecurity tools will make it through this
Between cybersecurity clients cutting back on their tool stack and some cybersecurity companies being unable to cater to remote workers, some cybersecurity companies won’t make it through this.
It’s a harsh reality, but businesses will fail because of coronavirus. The inability to keep clients and pay employees might even have a purging effect on the industry.
Some companies might get purchased by larger companies, while others will disappear and those clients will be consumed by bigger fish.
But you and your company can work through this if you have a good plan in place and you start to address the serious security concerns that are happening right now because of COVID-19.
Take advantage of free offers from companies when they are available, such as free DNS security. Share tips on how to work remotely and securely that both you and your employees can follow. Start protecting your company from threats now so you’ll come out the other side of this unscathed.
About the Author
Ken Carnesi is the CEO and founder of DNSFilter, a DNS threat protection solution that uses artificial intelligence to protect organizations from online security threats. Ken previously started the company Anaptyx in 2007 while attending Boston College, earning him a spot on EMPACT’s “30 under 30” list two years in a row. Ken is passionate about emerging technology and markets as well as car and motorcycle racing.


